(part of the Windows course :)
Note: if you don't have access to Windows Safe Mode - which is essential when cleaning viruses: before scanning with these applications I suggest you download and run from a flash drive Hitman pro. If it doesn't succeed try with a bootable CD running Kaspersky then launch the WindowsUnlocker feature. Only then you can continue with MalwareBytes.
Here is a list of free online anti-spyware tools that will help you to clean up a PC from spyware trojans and viruses. Compared with the standard anti-virus software they have the following:
- Advantages:
- no need for application installation on your computer.
- online scanners use the latest antivirus definitions.
- Disadvantages:
- some online scanners like Kaspersky online scanner and Panda Active Scan list only viruses they find without cleaning them. (Panda Active scan actually only finds viruses but cleans up spyware). This way they could be used for a system check only.
The following compact anti-spyware tools have a small size that will not affect your system's performance, and will not slow down your application loading time. So give them a try and don't forget to update the definitions first! - A-squared Web Malware Scanner
- SuperAntiSpyware makes a sophisticated spyware analysis on your system
- Anti-Spyware for the web from TrendMicro HouseCall
- Microsoft Security Essentials
- Norton's Symantec on-line security scan and virus detection
- F-Secure Online Virus Scanner
- ArcaMicroScan (first you need to download and install the supporting libraries)
- ESET / NOD32 Online Scanner
Some of the online scanners require specific access to run. Under Windows, if you notice at the upper part of the screen the Information Bar click on it and select Enable, Install or Run the file from the context menu.
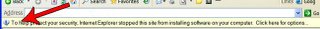
Some online scanners work in Internet Explorer browser only and require ActiveX controls to be turned on. You can enable ActiveX by switching to menu Tools on Internet Explorer:
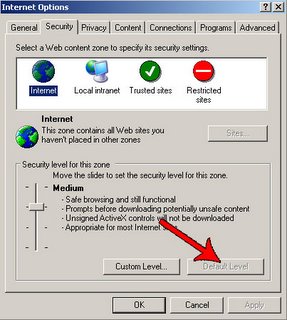
1. Go to Internet Options.
2. Then on the Security tab, click on Default Level.
Another way of enabling ActiveX is to add the antivirus program's website to your Trusted sites:
1. Go to Internet Options -> Security Tab -> Trusted sites.
2. For the Security Level for this zone click on the button Custom level...
3. Fill in the full address of the website you want to have access to in the input field Add this website into this zone & uncheck the mark on Require server verification(https:) for all sites in this zone.
4. Check the availability of ActiveX scripting in Internet Explorer. In the field Security level for this zone click on Custom level button and under ActiveX controls and plugins enable:
Automatic Prompting for ActiveX controls
Download Signed ActiveX controls
Download Unsigned ActiveX controls
Initialize and run ActiveX controls that are not marked as safe
Run ActiveX controls and plug-ins
Script ActiveX controls marked safe for scripting
Virus removal tools
If you really know what virus has infected your PC you can browse through major antivirus providers databases and download tools that will specifically clean up your computer at a much higher speed. Sometimes there are some virus variants that are not so easy to clean up so you can try downloading several different cleaning utilities in order to have a broader spectrum for catching the intruder. These tools need to be downloaded and run as standalone applications:
Avira
BitDefender
AVG
Kaspersky
McAffee
And if you think that you have infected file you can always send it for a check to:
https://virusscan.jotti.org/Protection tool
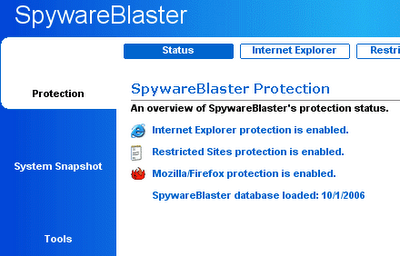
SpywareBlaster - prevents the installation of spyware, adware, dialers, browser hijackers, and other potentially unwanted programs. It will also protect your Internet browser.
Usage:
- Under “Quick Tasks” click “Download Latest Protection Updates”.
- Click the “Check for Updates” button.
- After updating, click “Protection” near the top.
- Under “Quick Tasks” click “Enable All Protection”.
How to save time?
Instead of testing all the on-line scanners you can first run a quick check & clean procedure with Dr.web's CureIt. Run the application and go to Options -> Change settings. Choose the "Scan tab" and Uncheck "Heuristic analysis". Then click on the Start Scanning button.
Last but not least you must definitely try the great free Anti-malware scanner/cleaner offered from MalwareBytes:
Happy cleaning!